Detect
Respond
Plan
Build
Trust
Threat Landscapes
Resources
About Us
Detect
Respond
Plan
Build
Trust
Threat Landscapes
Resources
About Us
June 2, 2024

The information provided in this article is intended solely for awareness and education purposes. Please note that sirar by stc shall not bear liability for any use or misuse of the information provided hereunder without consulting sirar by stc’s experts. Furthermore, it is important to note that any possible risk arising from the use or misuse of the provided information will be at the reader’s own risk.
Lastly, any references made hereunder to any entity/brand are solely for the purpose of providing corroborative context, with no malicious intent to defame or tarnish the reputation of such entity/brand.
– Invest in enhancing employee awareness to effectively identify phishing and spear-phishing emails.
– Empower your Microsoft Office 365 (M365) administrators by expanding their expertise across subscribed Microsoft cloud services. This enhances their ability to swiftly identify and respond to any unusual activities.
– Enable 360-degree visibility and actionable monitoring throughout Microsoft 365 (M365) cloud services.
The article discusses the changing security environment for cloud services, focusing on the notable rise in phishing attacks directed at platforms such as Microsoft Office 365 (M365). Even with the implementation of Multi-Factor Authentication (MFA), attackers have devised advanced techniques to circumvent these security measures through tools like EvilProxy. The analysis in the article demonstrates how attackers can utilize reverse proxy methods to intercept and manipulate genuine user sessions by bypassing the MFA. The article underscores the importance for organizations to bolster employee awareness, enhance M365 administrative capabilities, and establish comprehensive continuous control monitoring strategies to identify and address such threats effectively before adversaries had unauthorized access to the organization’s computing and IT environment.
In recent years, there has been a substantial increase in cloud services adoption, driven by the exceptional advantages delivered by leading cloud service providers (CSPs). These advantages encompass slashing capital expenditures (CapEx), providing the technical convenience of not needing to build any physical infrastructure, and cutting down costs related to day-to-day operations (OpEx). Moreover, cloud providers have gone above and beyond in many countries by ensuring compliance with both local and international regulations. However, alongside these advantages, cloud services also present a gateway for attackers to exploit online platforms as an entry point for targeting organizations.
CSPs are putting their best effort into implementing various security measures to minimize the attack surface. One of the well-known security measures that has been widely and effectively used is Multi-Factor Authentication (MFA). However, relying solely on MFA is no longer as effective as it once was. Since late 2022, attackers have been utilizing Phishing-as-a-Service (PhaaS) providers that leverage a tool named EvilProxy to bypass MFA security control for different cloud services such as M365, Google, Instagram, Dropbox, and others. This article will focus on examining the effect of M365 services in detail.
Let’s briefly examine the disturbing statistics that underscore the severity of the current situation, w.r.t., MFA, and increasing phishing attacks:
– MITRE ATT&CK, reported that a threat group known as LAPSUS$ has spammed target users with MFA prompts. Scattered Spider group sent repeated MFA authentication requests to target users, hoping that the legitimate user would allow necessary approval.
– Throughout Q3 and Q4 of 2023, a surge in phishing attacks impersonating essential cloud services, including Microsoft Office 365 (M365), targeted organizations with heightened frequency and sophistication.
– In July 2023, Menlo Security HEAT Shield detected and blocked a new phishing attack leveraging an open redirection vulnerability on the ‘indeed.com’ website, which redirected victims to a phishing page impersonating Microsoft.
The technical analysis of EvilProxy showed that it abuses reverse proxy to bypass MFA, where a threat actor operates as an intermediary layer between the victim and legitimate service, such as M365, commonly called a Man-in-The-Middle (MiTM) attack. The following is the breakdown:
EvilProxy: is a framework designed to intercept communication between a victim and a legitimate cloud service.
Reverse Proxy: is a legitimate technique where a server acts as an intermediary, forwarding requests to a backend server and returning the response to the requester.
MFA: MFA adds an extra layer of protection to access online services. This is an additional security measure or layer requiring a second factor (e.g., a secret code, fingerprint) besides the password for login.
The observed attack vector of EvilProxy involved phishing and spear-phishing emails delivered to victims. These emails contained embedded links or QR codes containing links impersonating legitimate cloud services. However, it’s important to note that this is not the sole method of infection.
EvilProxy framework is available for a subscription fee. However, the misuse of the reverse proxy technique is possible using different free open-source tools. The user-friendly nature of such tools, which come equipped with pre-loaded kits, makes it effortless for unauthorized users to use them.
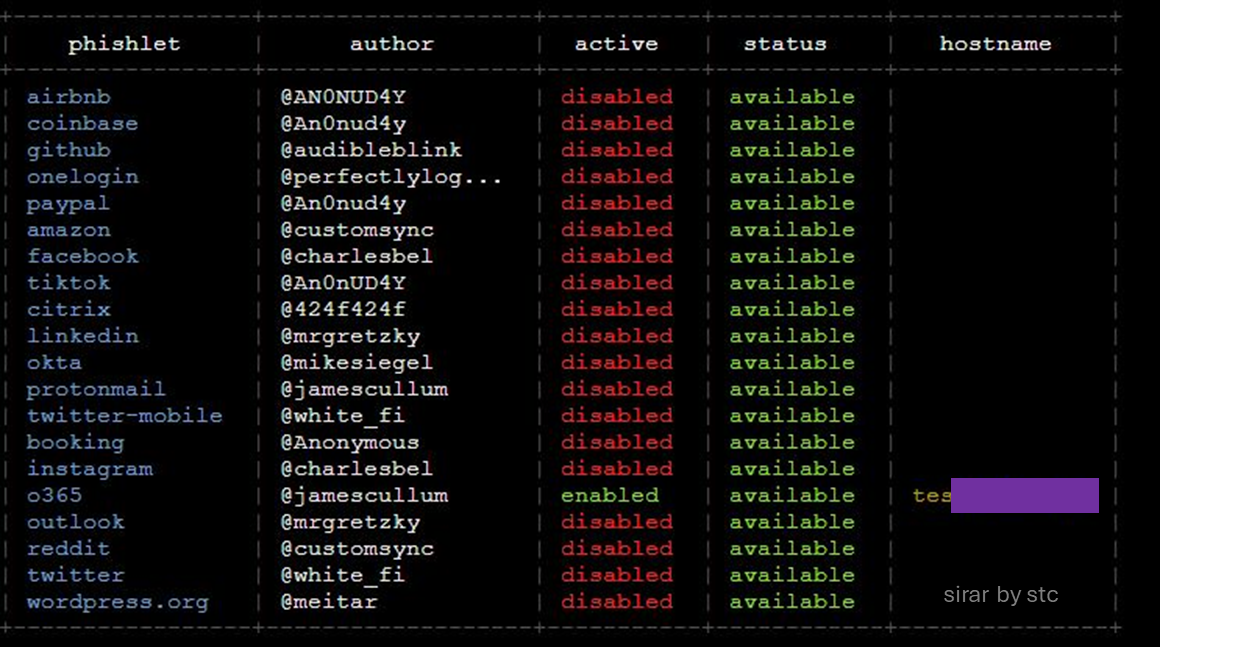
EvilProxy was observed to be used globally with different targeted cyberattacks to achieve different objectives, including credential theft. The following is the typical chronological sequence of an EvilProxy phishing attack:
1- The Phishing Email [T1566]
EvilProxy actors rely on human factors for their campaigns to be successful. Attackers tend to send phishing emails to convince users to click links that will open the website of a legitimate online service.
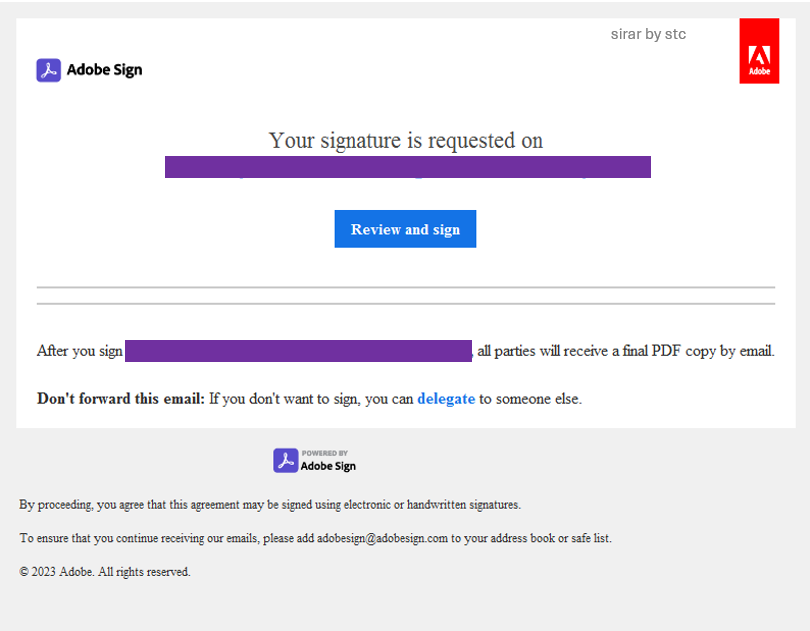
a. Impersonating legitimate services
Many organizations rely on different online services, such as Adobe Sign, as part of their day-to-day operations. Given that some of these services can integrate with M365, users are accustomed to utilizing their M365 accounts across different platforms.
b. Scanning Evasion
An additional phishing tactic involves persuading users to click on links outside of the corporate email application (e.g., Microsoft Outlook on a corporate laptop) in order to circumvent email security link checks. This is accomplished by embedding a hyperlink or QR code and asking victims to scan it using their phones. This effectively bypasses critical corporate security controls, like email and web filters, directing victims directly to phishing sites. By circumventing these safeguards, attackers significantly increase their success rate.
Alarmingly, the phishing attack utilizes dynamic redirection, which means, the links change rapidly with each request, redirecting the users to newly registered domains.
Hence, they can easily bypass the basic email and web security detection rules, especially in cases where they are not well-configured and fine-tuned. The redirections followed the same pattern in the analyzed samples:
a. The Phishing page – Always newly registered
Free tools would easily generate a phishing link based on a registered domain and configure it so that the selected cloud service can use legitimate cloud service resources. In this case, the landing page of the phishing link would be identical to the legitimate service as it uses its resources in terms of looks and feel, which would be hard for normal users to differentiate.
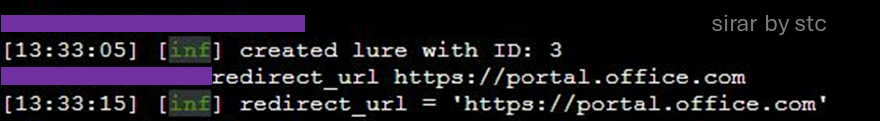

b. The redirection – Using well-known websites
Threat actors have been noticed to use open redirect flaws on well-known websites to redirect victims to the generated phishing websites.
2- Web Session Cookie [T1550.004]
After the victim lands on the phishing page and successfully provides valid credentials, the attacker will proxy the provided information to the legitimate service. It will, in turn, trigger the legitimate MFA verification service. It adds a fake sense of an additional level of security and authenticity, making the victim think that the page is legitimate.
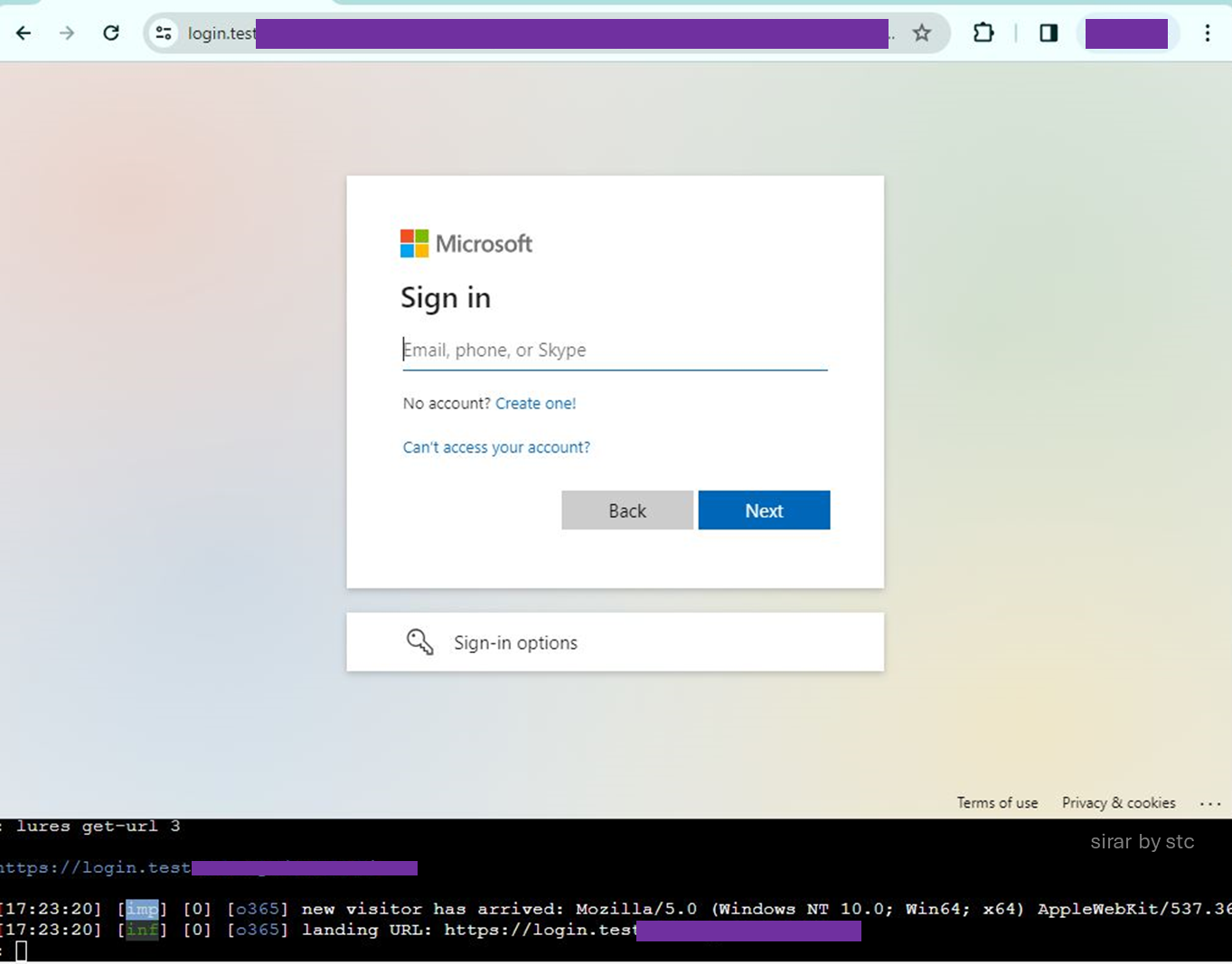
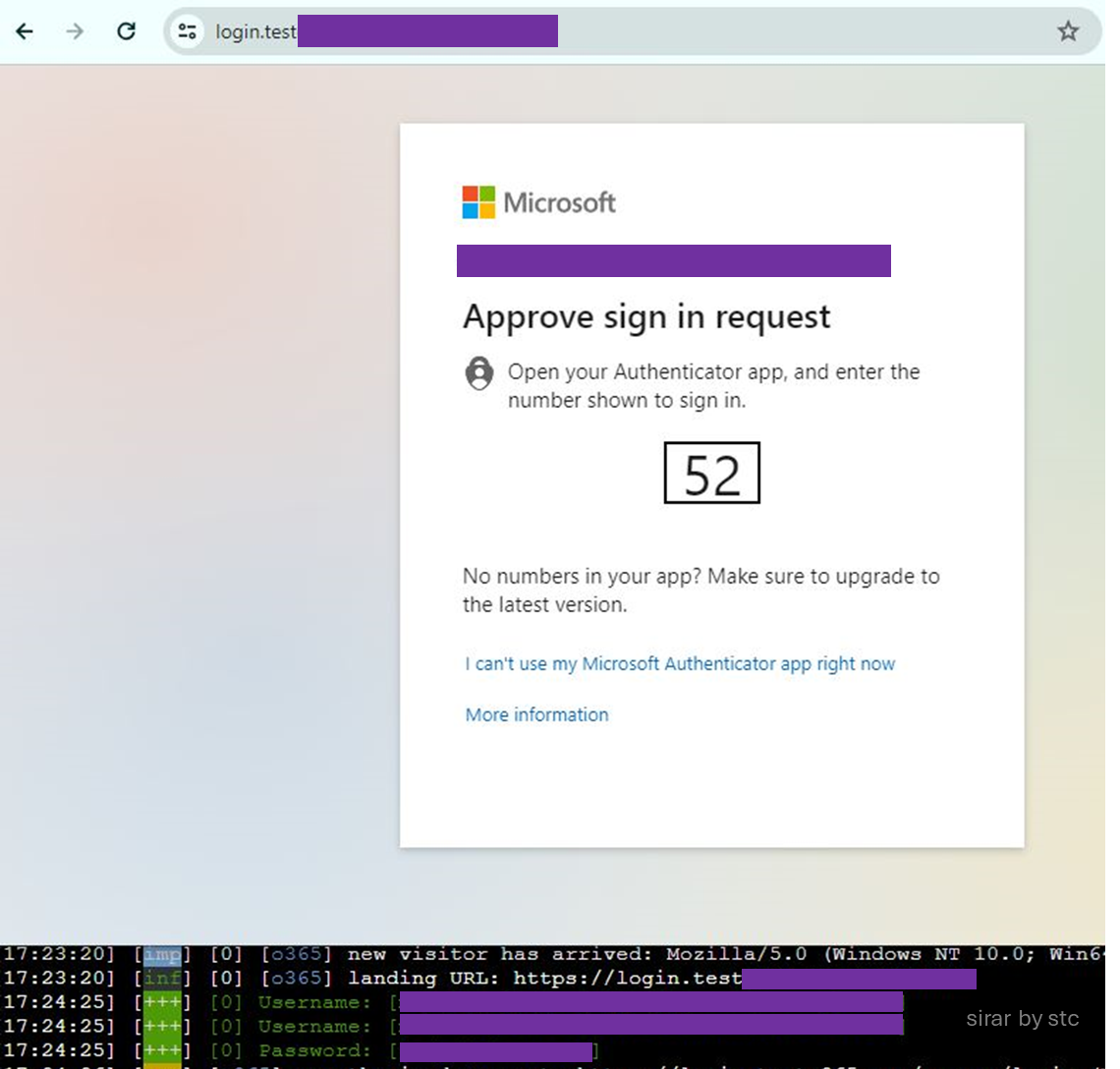
As soon as the provided credentials and MFA match as well as the victim is authenticated and authorized, the legitimate website (M365) will create a new session for the victim. The attacker will then capture that session information and redirect the victim to either a page mimicking the legitimate service or terminate the victim’s session.
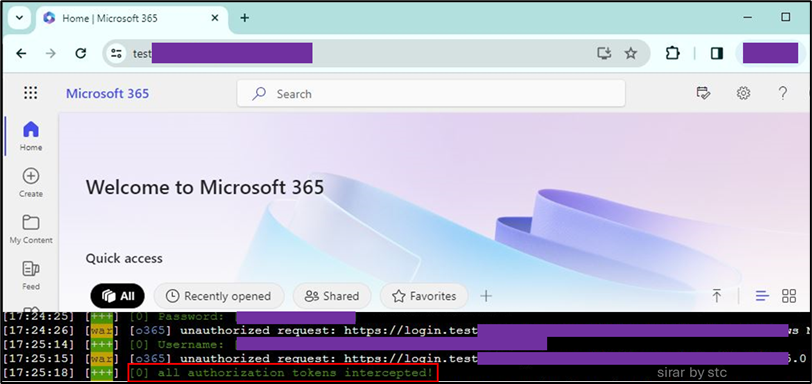
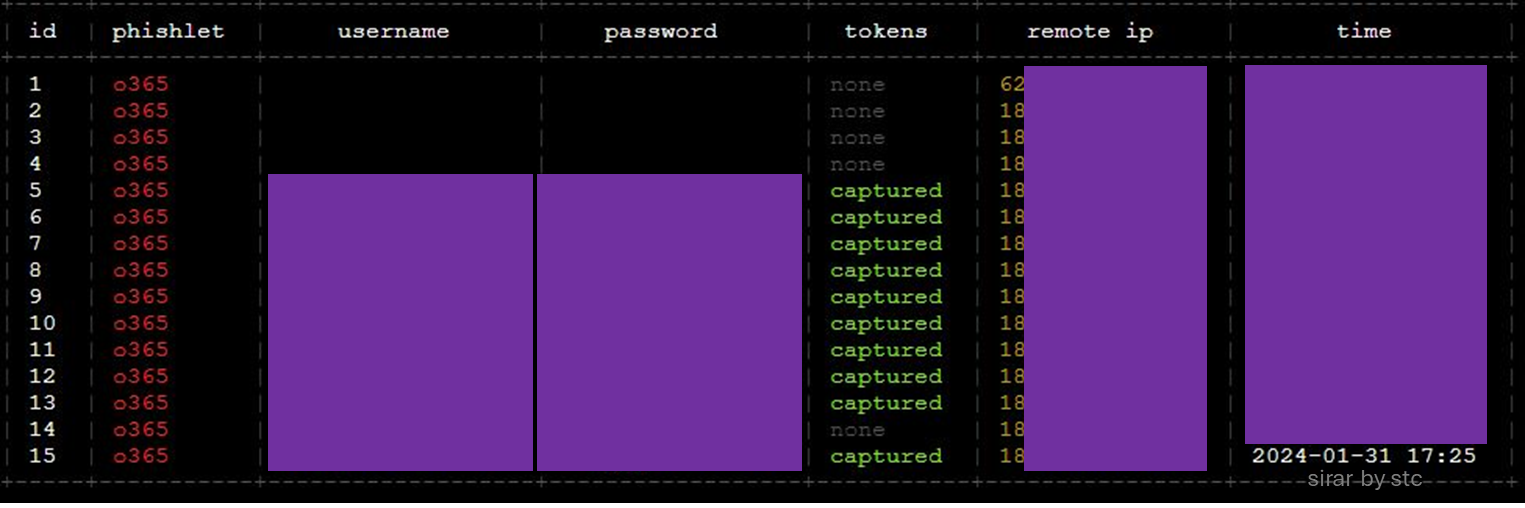
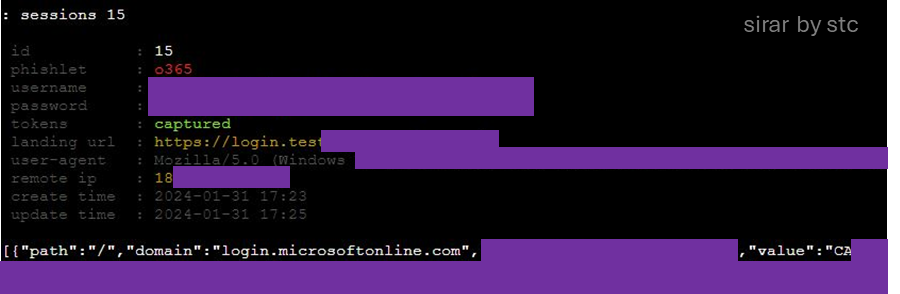
At this stage, the attacker can successfully login using the compromised account by re-using the session cookie information. Once imported successfully, the session will be activated, and the attacker will have full access to the resources assigned to the victim.
3- Modifying The Authentication Process: Multi-Factor Authentication [T1556.006]
After stealing the authenticated session, the attacker could add additional sign-in methods to maintain persistence.
4- Post-Compromise Activities [TA0040]
After the attacker gains control over the compromised account, they would benefit from the same privileges as the victim. This potentially allows the attacker to view and export emails or even send emails across the organization, impersonating the victim. In addition, could access across confidential information.
From the M365 access logs standpoint, the successful fraudulent login attempt was logged from the phishing kit infrastructure as a source IP address, and the login was verified by confirming all authentication requirements provided by the victim.
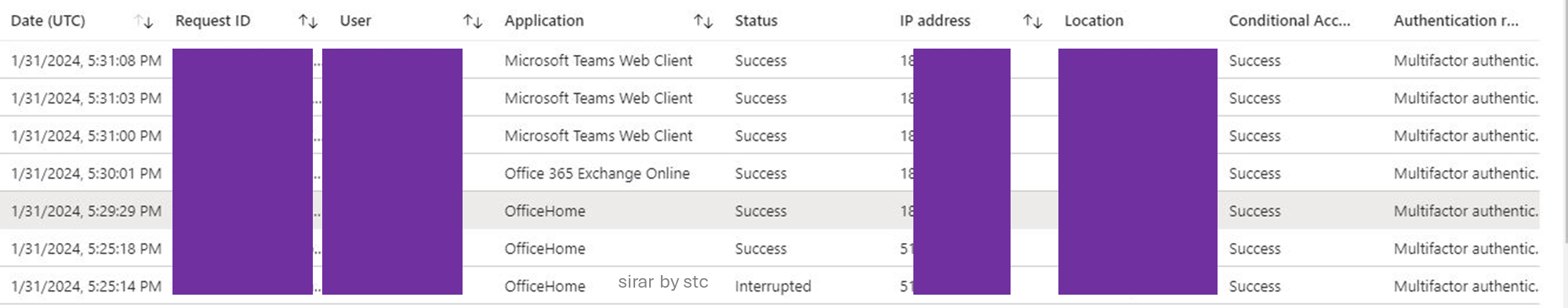
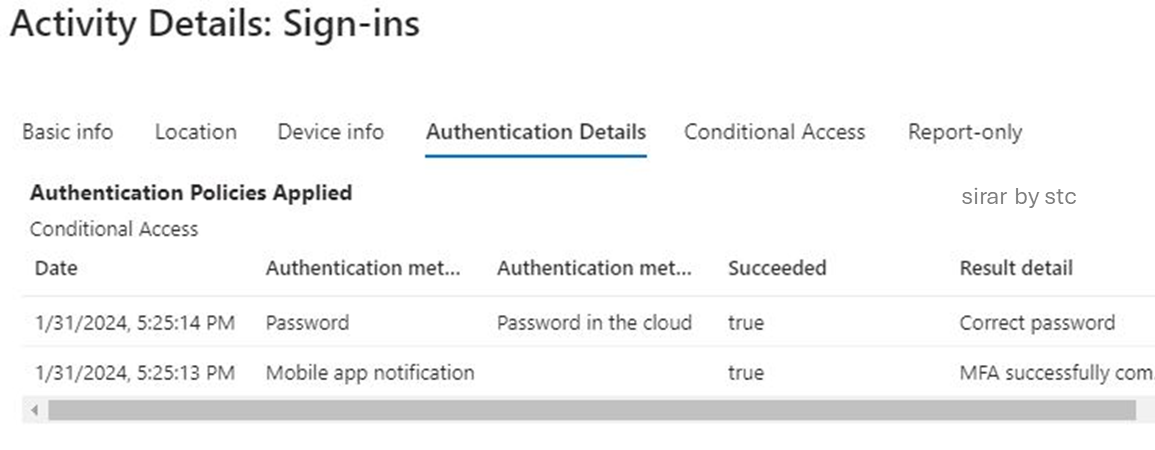
After checking the logs, another successful login attempt was made using the same application ID. Since the authentication requirements were satisfied previously, the session cookie was reused successfully.
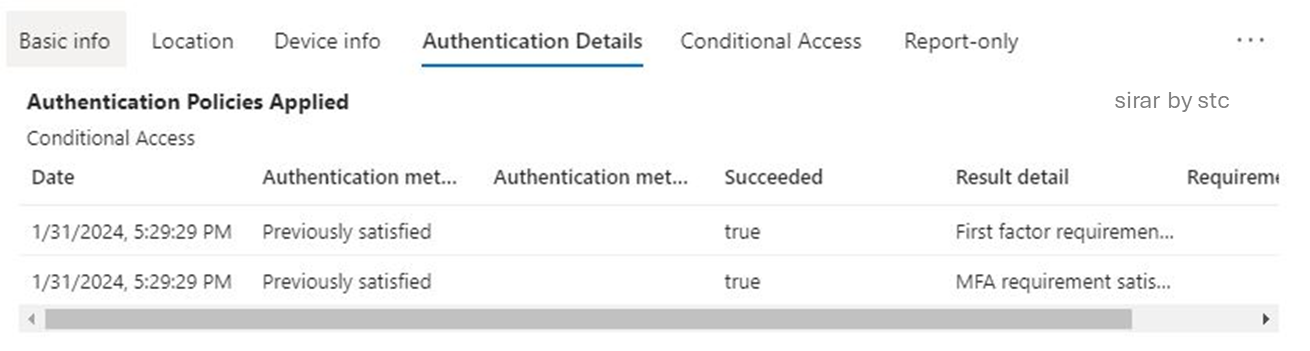
The examination of the session activities found that the reused session had the same unique ID as the one that was successfully captured during the phishing attempt. Yet the two attempts were initiated from different source IP addresses.

Although it is difficult to fully prevent phishing emails, M365’s extensive logging capabilities are a game-changer in the fight against phishing. M365 leverages these capabilities to proactively hunt for suspicious activities and identify potential phishing attempts before they wreak havoc. EvilProxy attacks rely on different techniques to succeed. However, instead of using a static Indicator of Compromise (IOC), which could be easily evaded, there are multiple behavioral characteristics powered by M365 capabilities that can be investigated to support in detecting such phishing attacks
– User Activities
M365’s risk-based policy measures could support the detection of risky behavior patterns, which automatically blocks any unusual sign-in attempts that deviate from users’ normal historical behavior patterns. It can also be configured to demand additional information to authorize the login attempt. As a prerequisite, it is important to configure the M365 user policy and allow M365 a period to understand the benign behaviors of a normal user.
– Application IDs
M365 has a unique identifier for each application. It has been observed that login using MiTM open-source tools would be shown as a legitimate first-party Microsoft application. Hence, it is worth checking and building use cases in different security systems, such as Security Information and Event Management (SIEM), to trigger in case an application ID is connected from two different sources within a short period of time. Besides, reviewing the active application lists on a regular basis is essential.
– Session IDs
Suppose the crafted phishing link is configured to redirect the victim to the legitimate M365 while the attacker replies to the session cookie. An audit log is a great resource for detecting such activities by filtering them using the suspicious session ID, as M365 would log all sessions under the same session ID.
– Email Detection [Safe link]
The email safe link feature scans incoming emails for any known malicious or suspicious indicators. Phishing links clicked from M365 Outlook will be scanned in the process. However, as threat actors use different phishing procedures (e.g., QR and newly registered domains), it is important to fine-tune email advanced persistent threat (APT) settings and its detection rules to detect such cases.
The following are important strategic recommendations to mitigate the impact of phishing and spear-phishing campaigns:
– User Awareness
User awareness has long been recommended to minimize the attack surface as it is considered to be one of the most effective security defense measures to prevent phishing campaigns. Investing in increasing users’ awareness by using well-structured content explaining the different effective techniques used by threat actors is crucial for effective phishing and spear-phishing detection. Wherever excellent awareness programs have been conducted, most phishing campaigns were detected by users even though different technical security measures were configured.
– Continuous Monitoring
The existence of SIEM does not necessarily mean that all anomalous activities will be detected effectively. It is important for organizations to invest in understanding logging capabilities for each system and service and to ensure their integration with SIEM solutions is effective by continuously fine-tuning its use cases.
– Policy Fine-Tuning
M365 comes with different capabilities for creating detection and prevention policies to proactively safeguard against a wide range of threats, including phishing. However, it is important to review all policies and evaluate their effectiveness regularly. Assessing and implementing Intune and conditional access policies greatly minimizes the attack surface.
– Consistent Reviews and Audit
Invest in performing an ongoing assessment and review of cloud services logs and capabilities to ensure that existing technical countermeasures are effective.
– Incident Response Plan
All organizations could fall for any type of phishing attack due to inadequate technical security measures or human errors. It is important to plan for such cases by preparing a mature incident response plan and playbooks.
Phishing campaigns employing MiTM technique are not new and will not stop any time soon, as open-source tools are continuously growing and becoming easy to access and misuse by anyone. While MFA remains an effective security measure for safeguarding online services, it’s insufficient to rely solely on it for comprehensive protection. Supplementing MFA with additional security measures can bolster the overall security posture of the organization.
It is crucial for key personnel within organizations to understand the significance of investing in cutting-edge security technologies. However, they must also consider putting efforts and investing in measuring the effectiveness of the existing security measures to eliminate the threat of phishing and spear phishing carried out through tools like EvilProxy.
– What is MITM (Man in the Middle) Attack | Imperva
– Multi-Factor Authentication Request Generation, Technique T1621 – Enterprise | MITRE ATT&CK®
– Bypassing MFA: A Forensic Look at Evilginx2 Phishing Kit | Aon
– Meddler-in-the-Middle Phishing Attacks Explained (paloaltonetworks.com)
– EvilProxy Phishing Attack Strikes Indeed – Blog | Menlo Security
– 2024: Taking on Evil Proxy | Arkose Labs
– EvilProxy Account Takeover Campaign Targets Key Executives – SOCRadar® Cyber Intelligence Inc.
– Resecurity | EvilProxy Phishing-as-a-Service with MFA Bypass Emerged in Dark Web