Detect
Respond
Plan
Build
Trust
Threat Landscapes
Resources
About Us
Detect
Respond
Plan
Build
Trust
Threat Landscapes
Resources
About Us
November 20, 2024

Cybersecurity revolves around three core principles, commonly known as the CIA triad: Confidentiality, Integrity, and Availability. Confidentiality ensures that sensitive information is accessible only to authorized individuals, while Integrity safeguards the accuracy and trustworthiness of data and its sources. Availability guarantees that information and systems remain accessible to intended users when needed. A significant threat to availability comes from Denial of Service (DoS) attacks, which aim to disrupt access by overwhelming targeted servers with excessive fake traffic. This flood of malicious requests forces the server to focus on handling the attack, leaving it unable to process legitimate user requests.
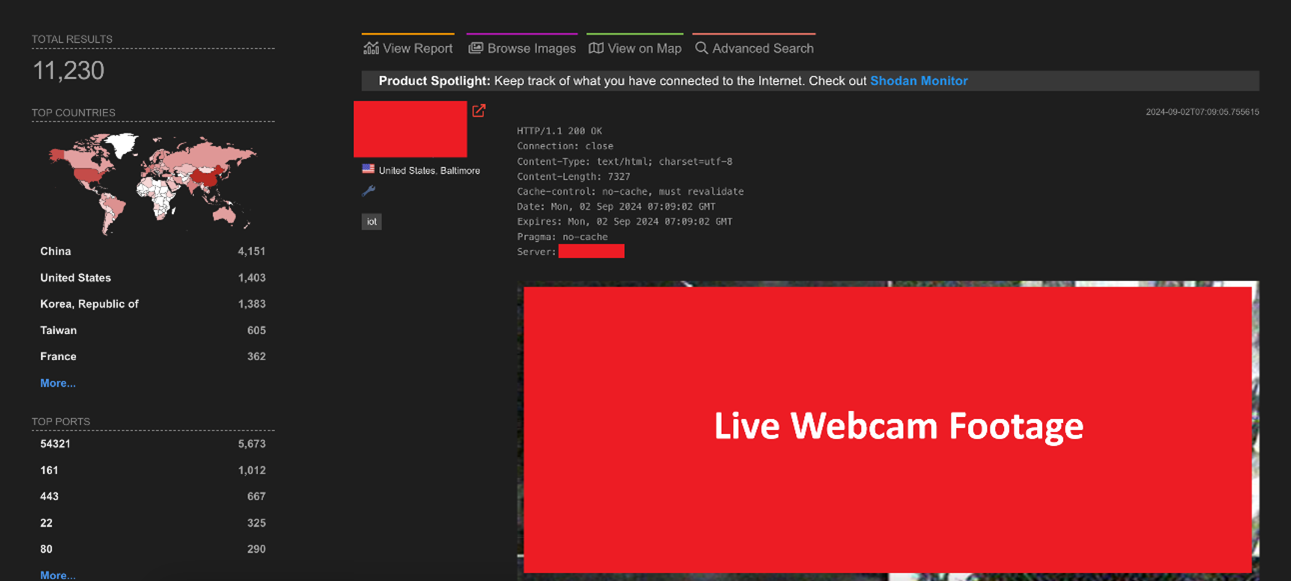
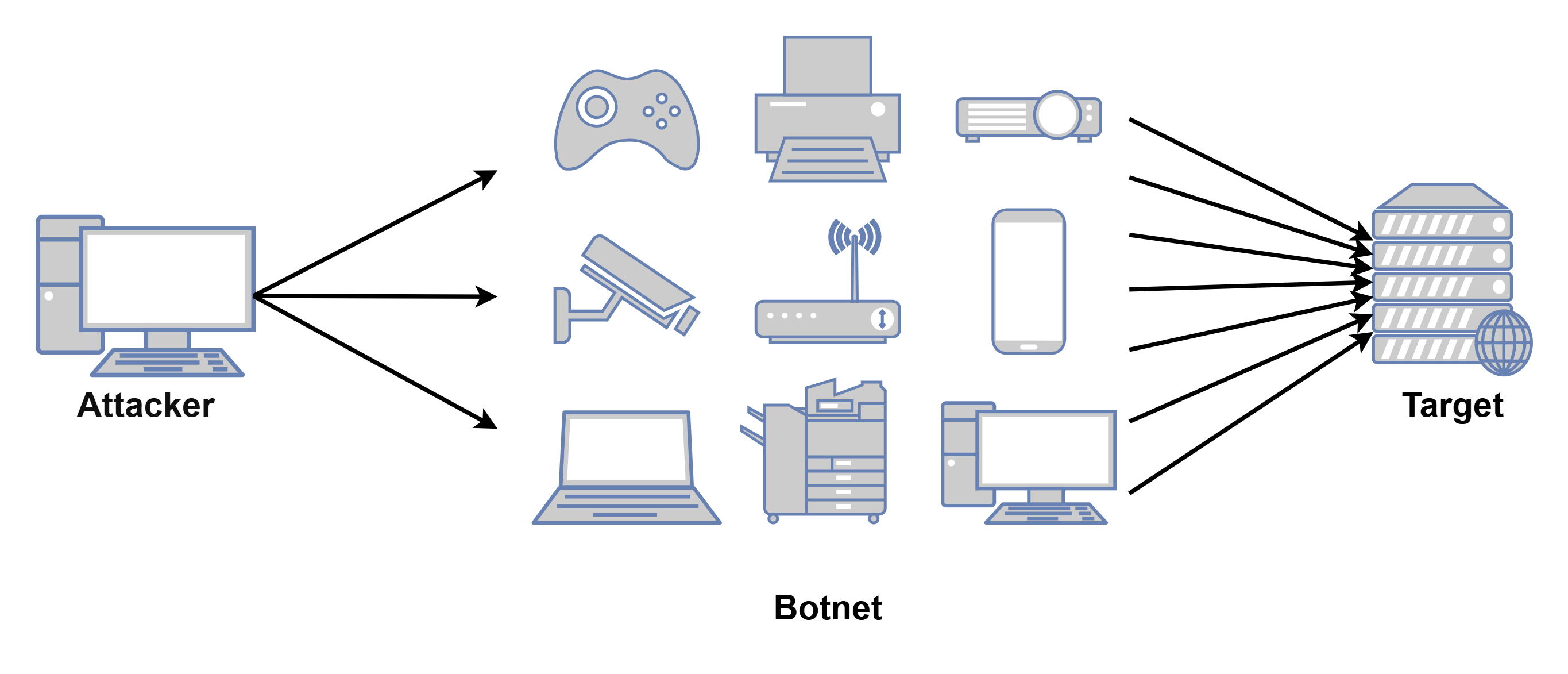
A Botnet is a term used for a network of devices connected to the internet, mainly misconfigured Internet of Things (IoT) devices, that are being controlled by a single machine (known as Command and Control / C&C server). Most IoT devices lacks the implementation of security controls making them easier to be compromised. With as simple as a keyword search in Shodan (a search engine for internet-connected devices) [figure 1] , attackers can search for any IoT device connected to the public internet with specific vulnerabilities.
Attackers usually use their C&C servers to launch DoS attacks using Botnets [figure 2] in order to amplify the number of requests making the DoS attack more affective and making it difficult for the target to locate the attacker due to the large number of devices connecting. These types of attacks are known as Distributed Denial of Service (DDoS). DDoS attacks can be mitigated but not completely prevented, since the public services need to be accessible to all devices around the world.
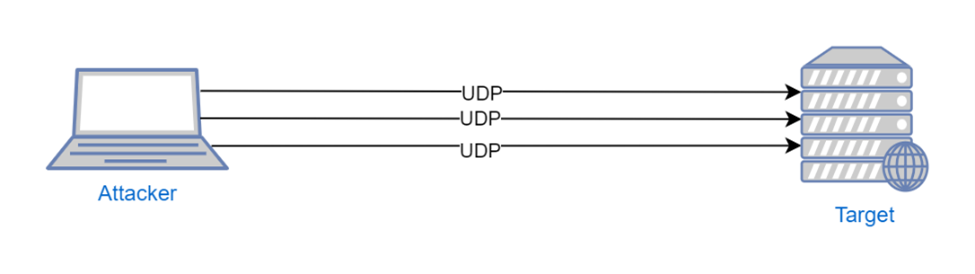
Most DDoS attacks are launched targeting a specific target server [figure 3], carpet bombing attacks however, are attacks that are sent to multiple targets with different volumes in the same interval [figure 4]. This type of attack is difficult to mitigate since it can use different DDoS attack types on several targets within the same infrastructure all at once.
There are several types of DDoS attacks, each type is done by misusing a network protocol:
Volumetric Attacks: These types of attacks are launched by sending a large number of packets for a specific protocol to a server. For example, since User Datagram Protocol (UDP) does not use authentication for connection, most devices will accept the incoming packets without validation. When an attacker launches a UDP flood attack, the target machine’s bandwidth could be consumed by the malicious packets [Figure 5].
TCP State-Exhaustion Attacks: the Transmission Control Protocol (TCP) is known as a reliable protocol since it authenticates/initiates the connection between the the Transmission Control Protocol (TCP) is known as a reliable protocol since it authenticates/initiates the connection between the client and server.
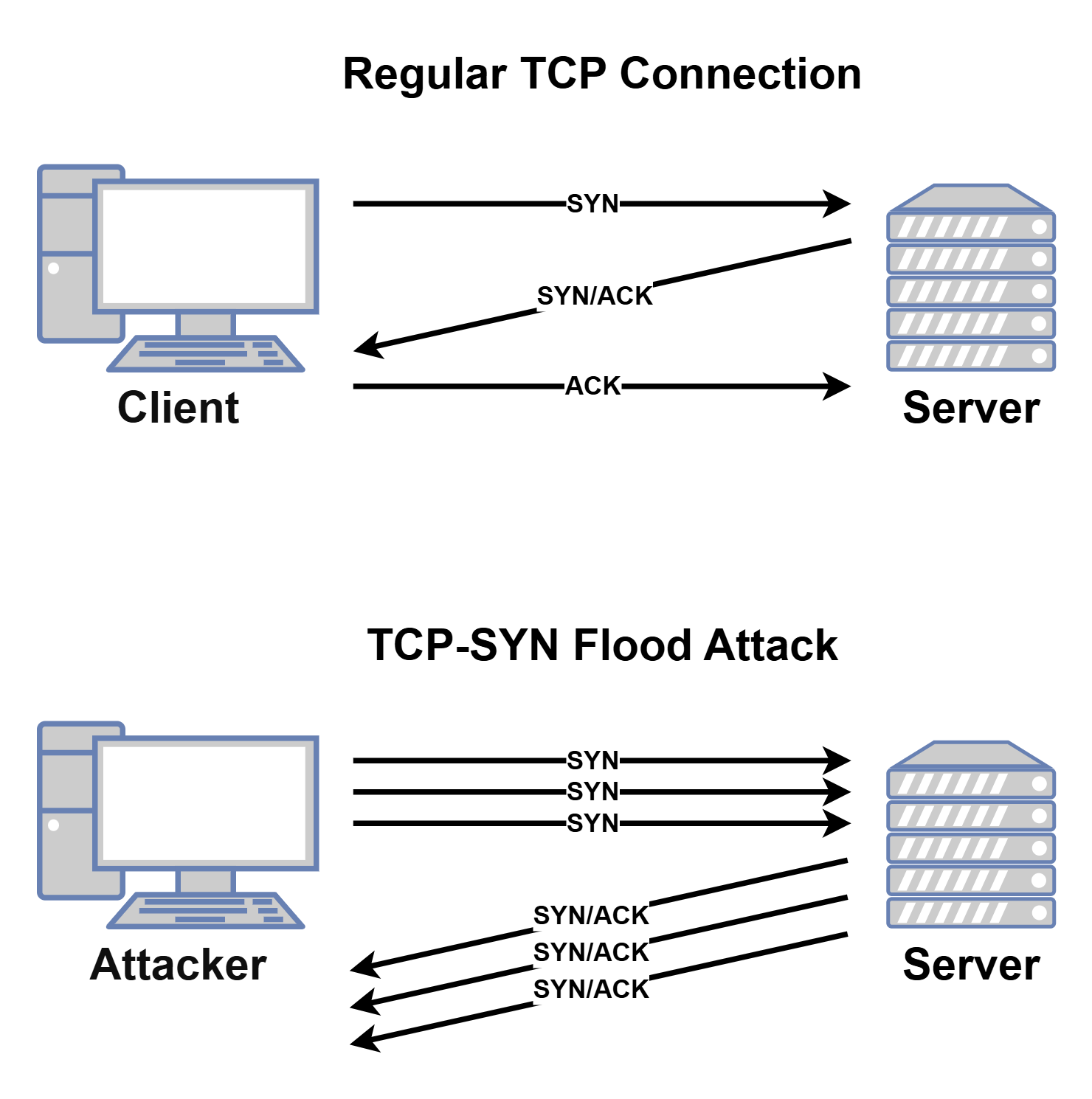
Hence it is the most used protocol due to it being a reliable protocol. In a regular TCP connection, the client initiates a three-way handshake by sending a SYN request, once the server receives the request, it will acknowledge the connection with a SYN/ACK response and starts a timer for the ACK response along with the data. Malicious actors perform SYN flood attacks by constantly sending SYN packets to the server for it to start a timer and wait for the SYN/ACK packets [figure 6].
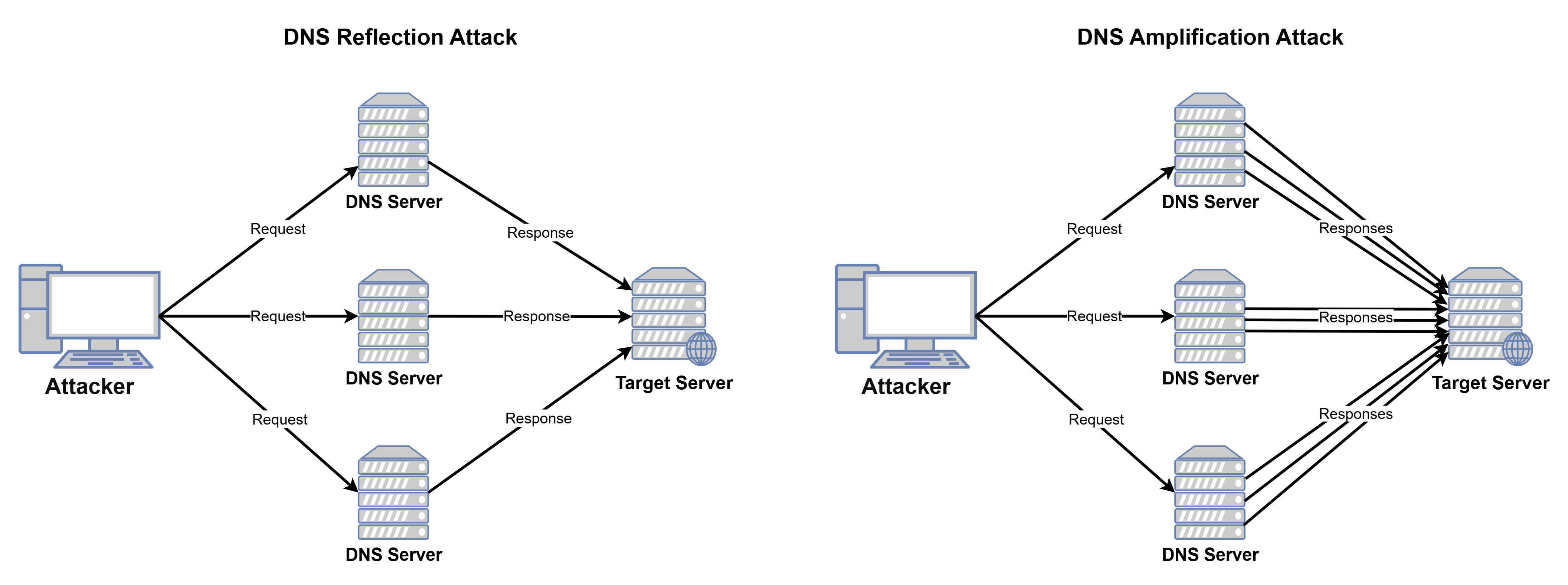
Reflection/Amplification Attacks: the attacker sends a response to a middle server and allows the response to be sent to the target server instead. Domain Name System (DNS) servers store the mapping between domain names and their corresponding IP addresses. DNS reflection attack is when the attacker sends a query to a DNS server, and the DNS server sends the reply to the target server instead of the requester. DNS amplification attack is when the DNS server sends the replies with a larger number than the requests which enhances the reflection attack [figure 7].
Application Attacks: as multiple application protocols evolve through time; application layer DDoS attacks are one of the most sophisticated attacks making them hard to detect and prevent. The most used application protocols are the web application protocols Hypertext Transfer Protocol (HTTP) and Hypertext Transfer Protocol Secure (HTTPS). When attackers launch HTTP flood attacks, they can customize several details in the request. For example, in the data inside the body of the packet, they send specific messages for taunting [figure 8] or make the traffic seem legitimate, etc.

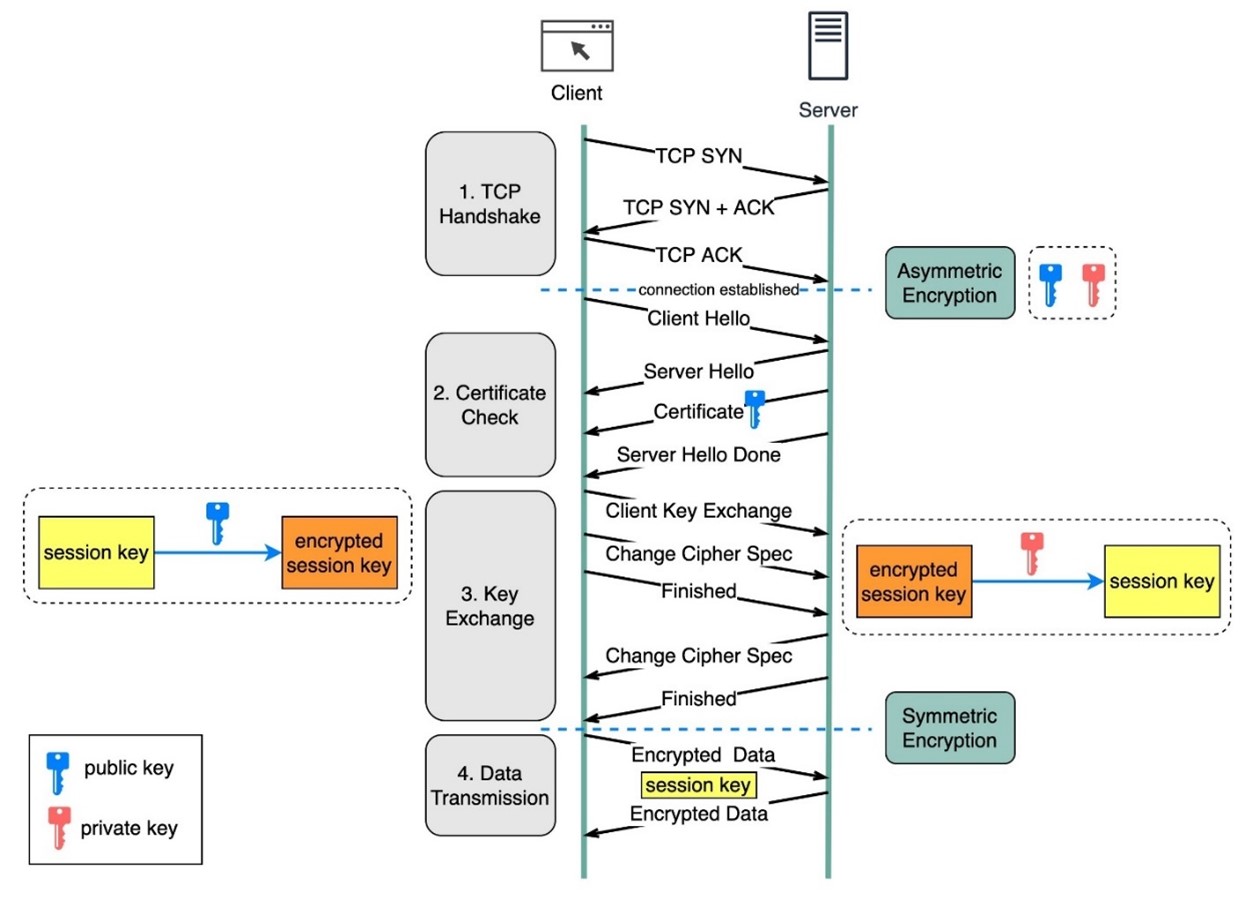
HTTPS is a protocol to enhance the security of the regular HTTP by encrypting the packet’s data using cryptography. HTTPS uses asymmetric encryption where a public key will be shared for encryption and a private key will be hidden for the receiver to decrypt the data. While HTTPS provides security, it can also be misused by abusing the encryption feature to launch DDoS attacks that can be difficult to detect and mitigate [figure 9].
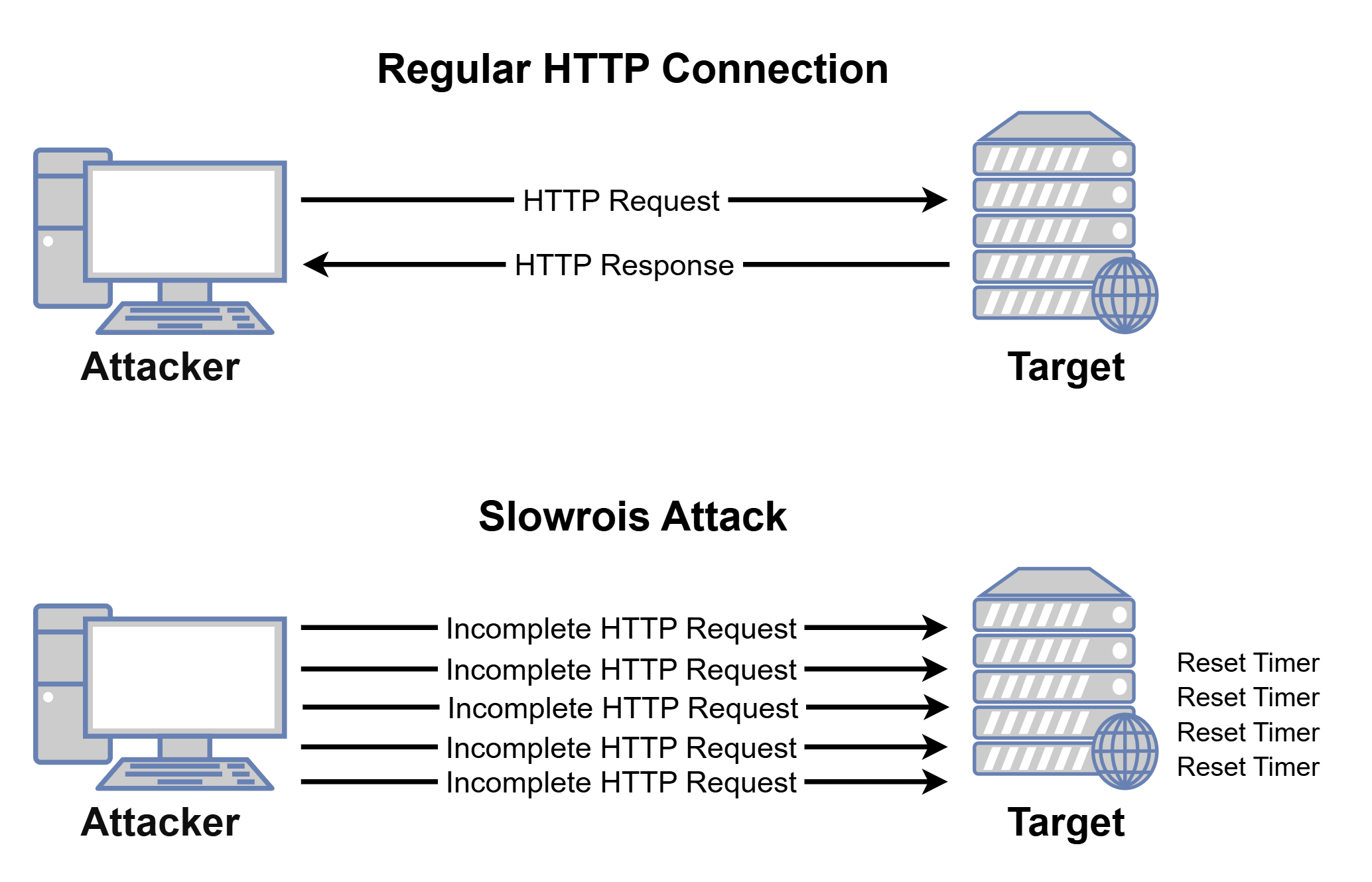
Slowrois is a known low bandwidth application layer DoS tool. The way this works is by periodically sending partial HTTP requests to the targeted web server. Since HTTP is a protocol that runs on TCP, the server will keep its timer running waiting for the complete HTTP connection. However, the tool will keep sending partial connections before the timer stops, making the connection never complete [figure 10]. The power of this tool is that it mimics legitimate requests by adding details of operating systems and browsers in the HTTP request headers.
After capturing and analyzing Slowrois attack network traffic [figure 10], we can see multiple connection establishment between the attacker’s source IP address “154.X.X.X” and the target server’s IP address “119.X.X.X” using the three-way handshake.
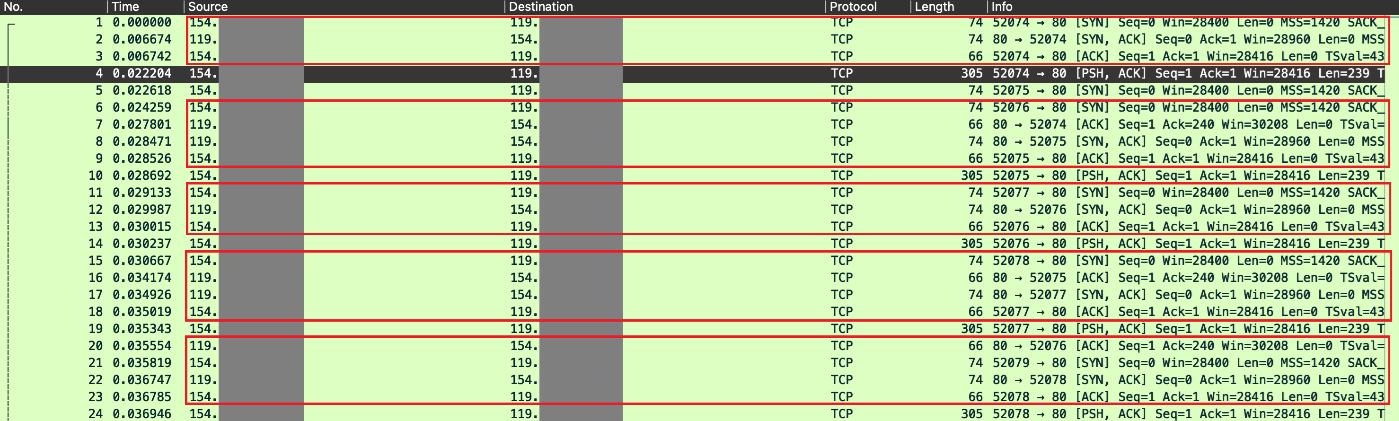
Right after the connection establishment, another packet is sent to continue the connection establishment process.
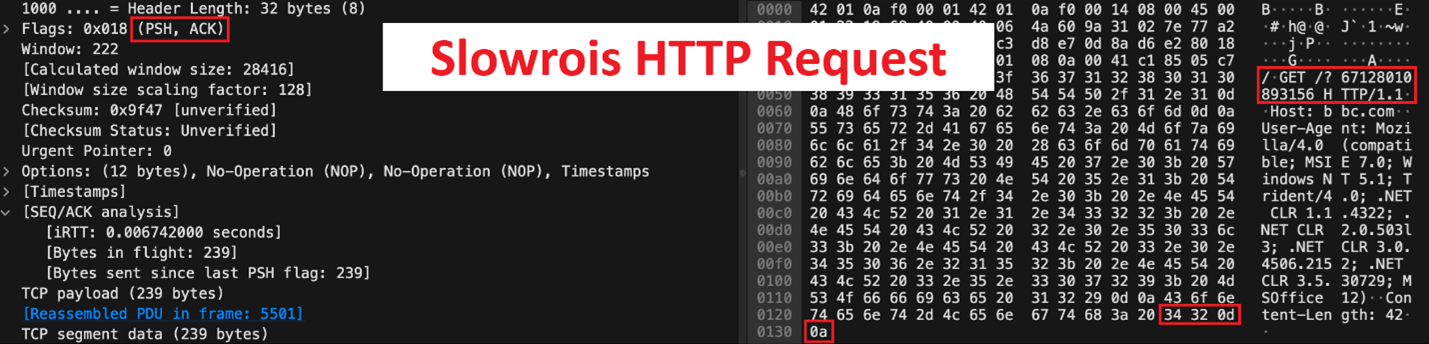
Once we analyze the packet [figure 11], we can see the following details:
– Flags = [PSH, ACK]: the “PSH” flag is to notify the server (target machine) to push the bytes to the application layer, and the “ACK” flag is to inform the server what is the last byte it has sent (to keep track of the data flow).
– GET request = “/?67128010893156”: the directory entered for the GET request is random and does not exist in the web server which indicates that the request is most likely forged and randomly generated.
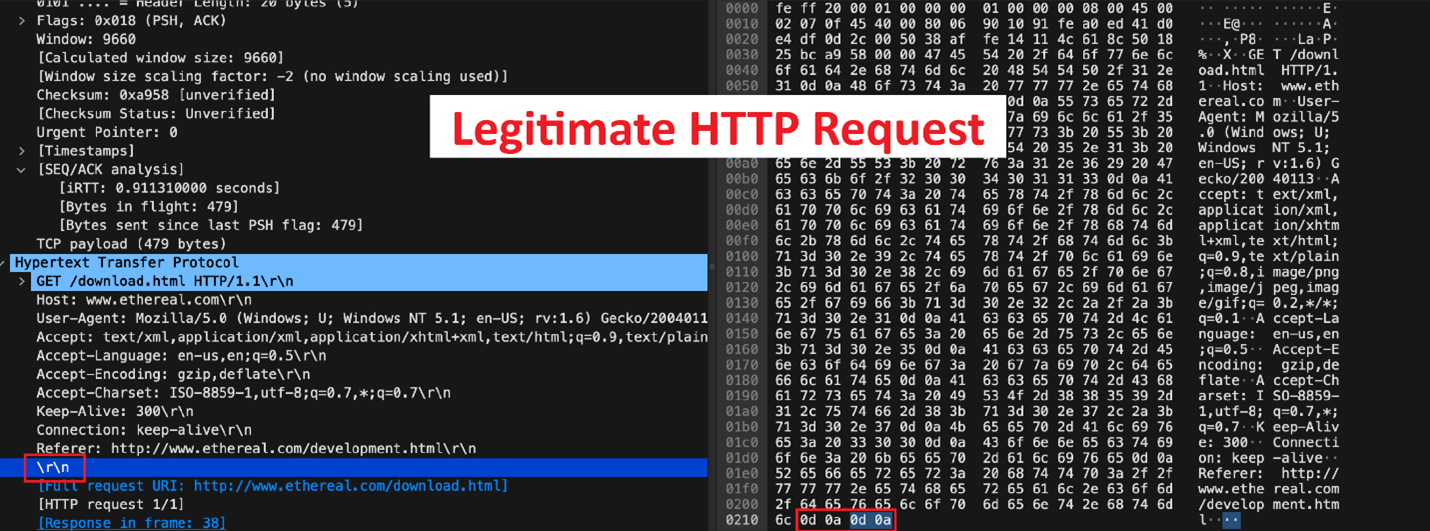
– Header’s hex dump ending with “34320d0a”: legitimate HTTP headers [figure 12] must end with “0d0a0d0a”. However, in our case we only have the first “0d0a” in the end of the HTTP packet header. “0d0a0d0a” indicates a line break “CRLF” which can be seen as \r\n in ASCII.
These incomplete [PSH, ACK] packets in Slowrois traffic result in the target machine keeping the connection open waiting for the full HTTP connection.
In regular TCP connections, there supposed to be another three-way handshake for connection termination where the client sends [FIN] packet, the server replies with [FIN, ACK] to acknowledge the termination process and the client sends back an [ACK] to fully close the connection. In this case however, the Slowrois network traffic does not contain a termination process as there are no “FIN” packets sent by the client’s (attacker) machine.
Network security in general remains an open problem in the cybersecurity realm. There has been a large evolution in computer networks in the past years. However, as technology rapidly evolves, so does their complications; with evolving network protocols and applications, regular security devices cannot catch up with their vulnerabilities. Thus, the use of advanced security solutions, mitigation systems and experts are crucial for organizations to catch up with potential cyberthreats.
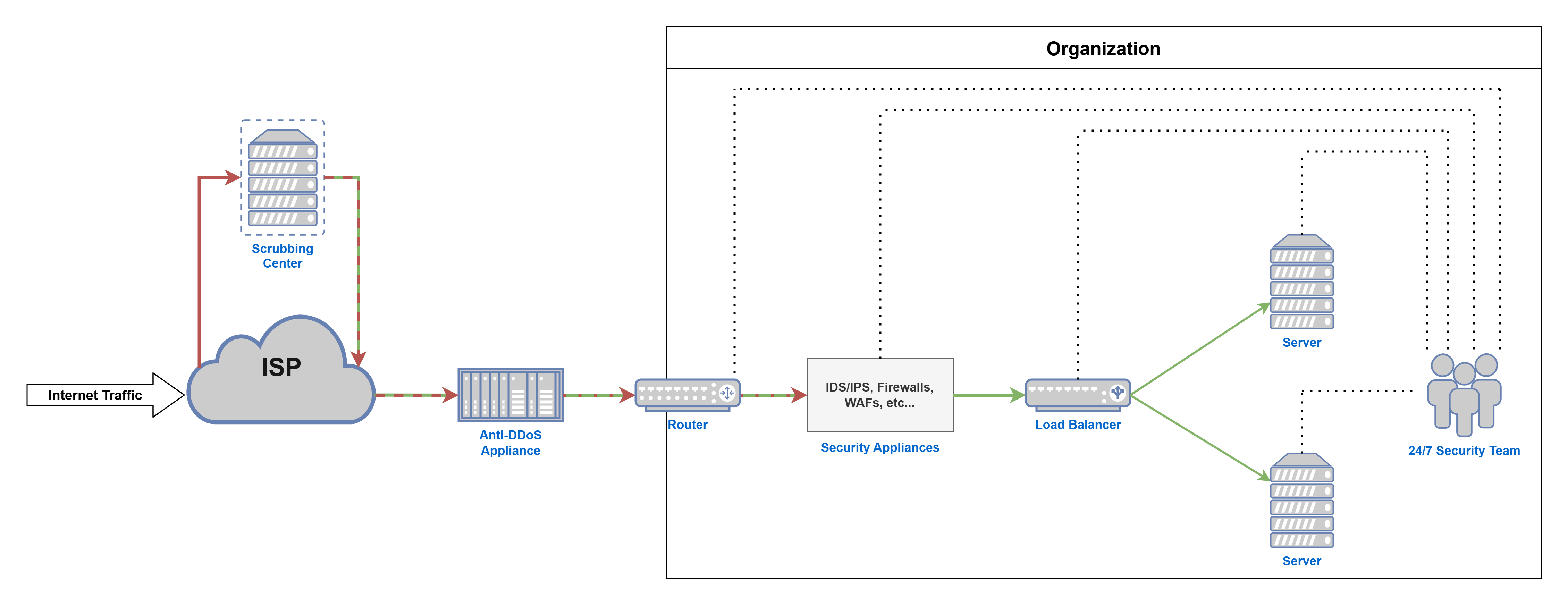
In order for organizations to mitigate their digital assets from DDoS attacks, they would require a scalable multi-layered approach [figure 13] (may differ depending on the organization’s infrastructure and design):
– Traffic Filtering and Rate Limiting: filter inbound network traffic by adding access control lists (ACL) on network devices such as routers and firewalls which will limit which IP address can communicate with the internal network.
– Stateful Packet Inspection (SPI) Firewall: SPI firewalls are able to analyze the packets’ headers and keep track of their connections over a period of time which can help in tracking and blocking unwanted connection behavior.
– Web Application Firewall (WAF): WAFs are dedicated security appliance that inspect web application traffic. This is crucial for Layer 7 DDoS attacks as they can check the legitimacy of the HTTP/HTTPS requests and block malicious traffic targeting web servers.
– Intrusion Detection/Prevention System (IDS/IPS): IDS is a security appliance that can detect and notify administrators for any unusual inbound traffic behavior. While IPS can detect and prevent the malicious traffic.
– Anti-DDoS appliance: There are dedicated an ti-DDoS devices that can be on-premises or cloud based by a service provider that are able to detect and protect against the different types of DDoS attacks.
– Load Balancing: load balancers redirect network traffic to another backup network/server in case of a high traffic which can be useful in case of some low bandwidth DDoS attacks..
– Traffic Scrubbing: inbound traffic is redirected to data centers with dedicated anti-DDoS technologies that can detect malicious traffic and forward clean traffic to the network/server.
– Security Specialists: with all the technologies in place, for business continuity, it is crucial to have a dedicated network security team that monitor network traffic 24/7 for quick incident response and handling.
Statistics show that there has been a significant growth in launching DDoS attacks on organizations around the world:
– Sirar by stc has captured 40115 DDoS attacks in 2022 and 47716 attacks in 2023, showing a 19% of increase of DDoS attacks within a year.
– The average attack volume sirar by stc has captured in 2023 has increased by 121% within a year where the largest attack was 417 Gbps.
– More than 6600 hours of downtime due to DDoS attacks have been prevented by sirar by stc’s anti-DDoS service in 2023.
– It has been calculated that the downtime of organizations due to DDoS attacks cost around $40,000 per hour in average.
As computer networks and applications evolve, cybersecurity also grows in complexity. With the increasing complications of network protocols and vulnerabilities, traditional security controls are unable to keep up. Organizations have a continuous problem in securing digital assets from growing risks such as Denial of Service (DoS) attacks. DoS attacks aim to overwhelm systems with illegitimate network traffic, leaving them unable to respond to legitimate users. Malicious actors enhance the damage by utilizing scattered devices around the world by to perform different types of DDoS attacks, such as volumetric attacks, TCP state-exhaustion attacks, reflection/amplification attacks, and application layer attacks. To mitigate the threats caused by DDoS attacks, organizations must take a multilayered defense strategy which includes traffic filtering, stateful packet inspection firewalls, load balancing, traffic scrubbing, specialized security teams who monitor traffic and respond to incidents in real time. As technology advances, staying ahead of the latest cybersecurity threats will need ongoing monitoring and investment in advanced security solutions and expertise.
-threat-landscapes-2023
-what-ddos-attacks-really-cost-your-busines
-learning/ddos/ddos-attack-tools/slowloris
-knowledgebase/slowloris-attack